After a more relaxed start to Cisco Live on day one, I expected a much more hectic atmosphere on day 2 and that’s exactly what I got. My focus for today and the general theme throughout the week is to see what Cisco has to offer when it comes to both Security and Cloud. I was also looking forward to the World Of Solutions opening to see what new innovations Cisco’s vendor partners are doing as well.
Before any seminars got underway the morning was focused on Keynotes, both the event Keynote and Partner Xperience Keynote. As I expected the opening Keynote was based on what Cisco will be doing in the upcoming year and on the foundation of digital transformation. My favourite part of keynote talks, in general, is always the customer case studies as it puts a realistic spin on what the overall message is. Which from my point of view was how Cisco is at the forefront of Digitisation and technology innovation.

The second Keynote was the Partner Xperience which was kicked off by Wendy Mars. This keynote was for Partners only and again I took so much away from this talk, which was one of the main sessions I wanted to attend. Cisco has held the discussions and seminars in a way that its customers and partners are getting valid and usable information, rather than just a ‘Marketing Message’ which I have experienced at other vendor events in the past. Don’t get me wrong there is a need for that type of message but my experience so far is that Cisco is getting a great balance in the seminars and talks.
The whole Partner Keynote was very much based on how Cisco can help its Partners in overcoming ‘Customer Challenges’ as well as Partner Challenges. My main takeaway from this keynote session was that when I am putting together a solution am I future proofing it? Am I thinking about the ‘end-to-end’ solution? Or just the specific problem at hand?. Something else to come out of this talk was how Cisco is evolving their approach, and rather than solutions they are offering ‘Platforms’.
Automation was another key theme throughout the talk and ACI was touched upon for Data Centre level network automation but the final takeaway from this talk was the power of Data. One quote that really hit home for me was: ‘If you don’t collect data, what can you analyse?’ How true is that!? How do we know what threats are attacking our network if we don’t collate this information into a usable format?. Cisco has a vast range of products to aid partners and customers with these types of challenges.
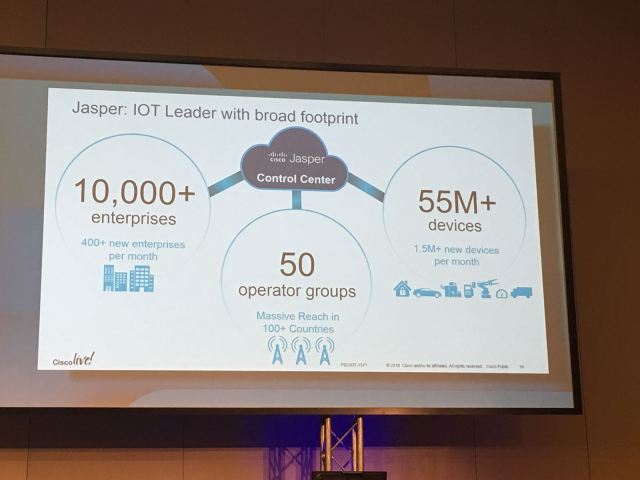
The Keynotes were now done for the day and my first session was one I initially had mixed feelings about when I put it on my schedule: ‘Unlocking the value of IoT Data’. The main reason for this being the fact that I am very new to IoT (Internet of Things) and wanted to understand more about it. This seminar was based on two Cisco products: Cisco Kinetic and Cisco Jasper. This was again my first experience with both of these products but I must say they are very impressive. Within these two products, Cisco covers both IoT for OT and IT networks (Kinetic) and IoT for Cellular networks (Jasper). The most eye-opening information for me was that one of the slides which had been updated this morning was already redundant. The slide in question showed how many Enterprises and devices were currently using the Cisco Jasper platform, however, the numbers had changed so much so that the numbers on the slide was extremely inaccurate – in half a day!! That is growth and it just goes to show that Cisco is at the forefront of IoT.
After lunch, I headed over to the World of Solutions which was by far the highlight of the day! I must admit at first I was fairly overwhelmed by the sheer amount of stands, people and different aspects of visiting. I just had no idea where to start! I, therefore, decided that with it only being day two that I should get my bearings a bit and just walk around and see what there is to offer. I have put some pictures on my twitter feed @shabazdarr with highlights of what was on offer.
Now I want to tell you about the most interesting part of my day which was my visit to the World of Solutions and my discussion with the Cisco Security team around their Email security products including AMP. They were kind enough to show me a demo of the products, but one thing I saw which was impressive was that even though an email has been allowed through the Email security appliance (be it cloud or on-premise), it continues to be monitored in case a threat has been missed. As soon as the threat is detected it is deleted!! Now, this could be hours or even days after the email has been received, but for me, I have not seen many products out there which offer this. Again the integration between products was very impressive, with Cisco AMP integration with Cisco Umbrella it just adds to the user’s security platform.
The final talk of the day was the C-Max theatre for ‘Changing the Security Equation’. To be honest there wasn’t much in this talk which I didn’t already know. It showed more detail around what products Cisco have to protect Networks and Infrastructures from Cyberthreats including the Next-Gen Firewall (NGFW), Cisco Umbrella and Cisco StealthWatch. It is great to hear about these products, but for me, I need to get my hands on them to really understand what they can offer, so keep an eye out for upcoming blogs this week after I have done some more hands-on labs!
That wraps up my take on day two. A really interesting start with the seminars and talks and it has given me a good platform for the rest of the week. For more information on today take a look at my twitter feed @shabazdarr and Concorde Technologies twitter feed @ConcordeTG.

Author: Shabaz Darr, Senior Professional Services Consultant at Concorde Technology Group



